Sabbatical, week 3
This week I’ve laid some good groundwork for Expirybot and had fun playing part-time security researcher.
Alright, I’m cheating a bit, week 2 is missing, but for some reason I’ve been struggling to write up that week. I’ll try and retro-post it later, for completeness.
This week has flown by but it’s been interesting and productive, with most of the week spent on Expirybot and security research.
Finished migrating my PGP keyserver to debian
I didn’t really want to have to do this, but unfortunately sks version 1.1.6 isn’t available on Ubuntu. Since I was stuck on 1.1.5 I got dropped from the public pool, meaning my server no longer received requests directly from members of the public. That didn’t directly break Expirybot, since I’m still receiving updates from my keyserver peers, but there’s other types of PGP improvement research which does depend in getting raw traffic.
I took the opportunity to move off Digital Ocean and get a new server inside the EU - with Hetzner, at an incredibly affordable 7 ish EUR per month for a 2GB machine. I managed to rebuild sks 1.1.6 and migrate keyserver.paulfurley.com without breaking too much. Shortly after, I’m back in the pool and once again receiving ~1% of global PGP keyserver queries.
PGP-signed Expirybot’s outgoing emails
This was harder than I expected, but I got quite a bit of independent feedback that my PGP expiry emails should be PGP-signed.
I spent the first part of the week building this, and a new web service for handling unsubscribes (necessary for signing the emails).
I’m now in a much better place for building new features for Expirybot, which I also started to test on people - more below. I spent a few hours on Friday writing up how I sign the emails.
Wrote a scraper for auction data, then went to the auction
This is a bit off-the wall, but I’m quite interested that there are houses for sale in Liverpool for less than £50K, and some of them are in areas that I believe have an excellent future.
I’ve never been to an auction, and it wouldn’t be right to go unprepared, so I built a scraper to analyse the listings before I went.
The auction was pretty exciting for two or three lots, then it got boring and I went home.
Nope, I’m not going to become a landlord just yet, but I am thinking about how to do it in a way that’s not morally bankrupt, doesn’t push up prices, and doesn’t make it harder for people to buy houses.
I had a good email exchange with the nice folks from Generation Rent asking for guidance on what they consider being an ethical landlord. I’d much prefer to build houses as an investment… now there’s a worthwhile enterprise … but that’s completely out of reach for me. For now I’m more interested in investing in green energy.
Investigated EE apparently leaking my phone number to a website
I had a fascinating, spooky experience on the internet that made me realise how internet security must feel for… lots of people.
_Somehow, _it looks like I clicked on a link on a website, and this alone subscribed me to a premium rate SMS service. I’m pretty outraged that this can happen, mostly because I’m concerned it means my phone number was transmitted to some Azerbaijan (literally) company’s website without my consent.
I’ve got some very intelligent input from some contacts (thank you folks!) and I’m planning a full write up on this, but for now, here’s the work in progress:
- Me asking on security.stackexchange.com (no answers yet)
- Me asking on community.ee.co.uk (seems to be getting some traction now)
- Interesting paper: ‘Privacy Leaks in Mobile Phone Internet Access’
- Another: ‘Header Enrichment or ISP Enrichment? Emerging Privacy Threats in Mobile Networks’
Reported a probable security breach at the Gym Group
I’ve enjoyed playing part time security researcher this week!
I use unique email addresses for everything in order that I can figure out who spams me, and block that email address. I’ve got between 5 and 10 addresses now which have been compromised so I bounce them, much to my satisfaction.
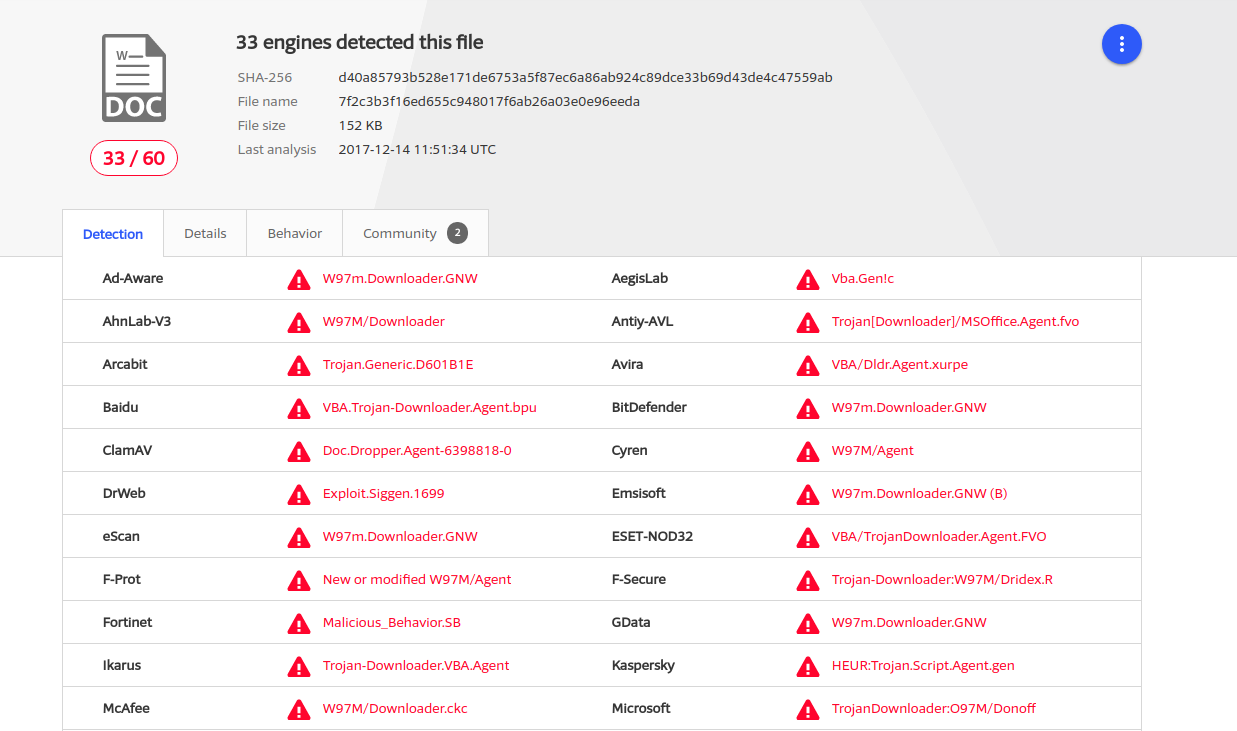
This week I received an email to the unique address I used to use for the Gym Group, which I left years ago. It was a classic malware email, a friendly note asking for the status of the attached invoice:
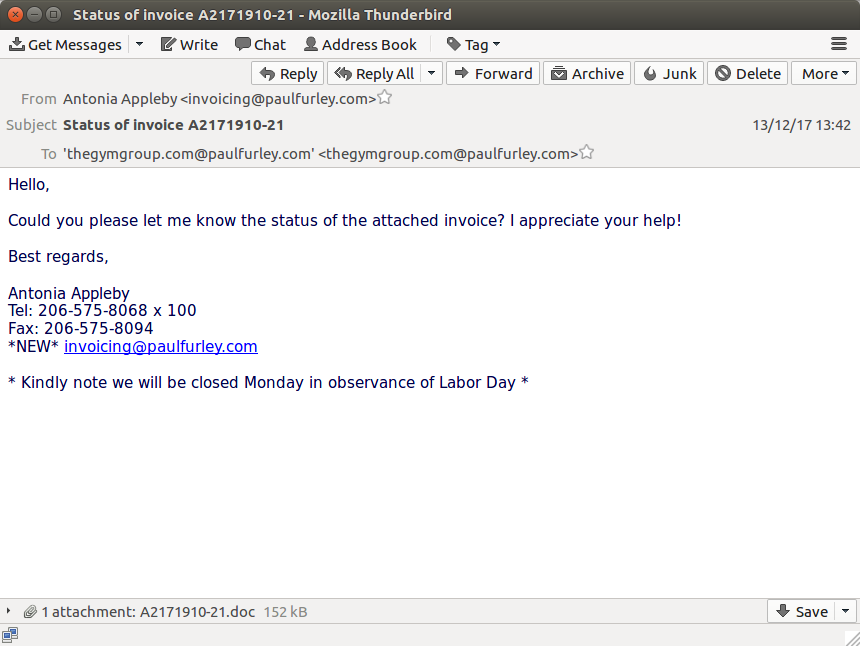
And, of course, it’s carrying some virus (virustotal.com).
I reported this to the Gym Group - slowly - and pointed out it’s a pretty good sign they’ve breached their customer database. I wonder if they’ll investigate and report this to the Information Commissioner’s Office?
If you’re reading this, Gym Group, top tip: take security disclosures seriously - you didn’t make it easy!
Asked for feedback on new Expirybot features
Over the last 6 months, as Expirybot has been sending people helpful reminders about their PGP key, some people have generously been filling out a little survey, helping me understand what they use PGP for and so on.
That data in itself has been really helpful, and in addition many of those people agreed to be contacted again.
I’ve been thinking of new things my Expirybot project could do, but unlike the current reminders, which are unsolicited, I wanted to get upfront permission to do more.
I emailed 50 of my respondents explaining that I’m working on six features, and would they like to sign up and give me feedback. To my delight, a few people have already replied saying yes, and I’ve got some good, granular feedback on which features people are interested in. Awesome!
Here’s the list - if you’ve got any feedback, let me know!
- Email people earlier - like 30, 14, 7 days
- Notify people when a potentially suspicious new key is added with your email address
- Provide ICAL calendar feeds for keys
- Notify people their key’s cipher preferences (eg SHA1) are no longer considered secure
- Inform people their (unsafe) short ID is being queried in the keyservers, and helping them correct it
- A command-line tool (GPG wrapper) to generate, rotate / extend your primary key and subkeys automatically
- A teams tool for monitoring all the keys for an organisation e.g. @yourdomain.com